
Photo by Dennis Kummer on Unsplash
Common Security Risks and Mitigation Strategies for AWS S3 Buckets
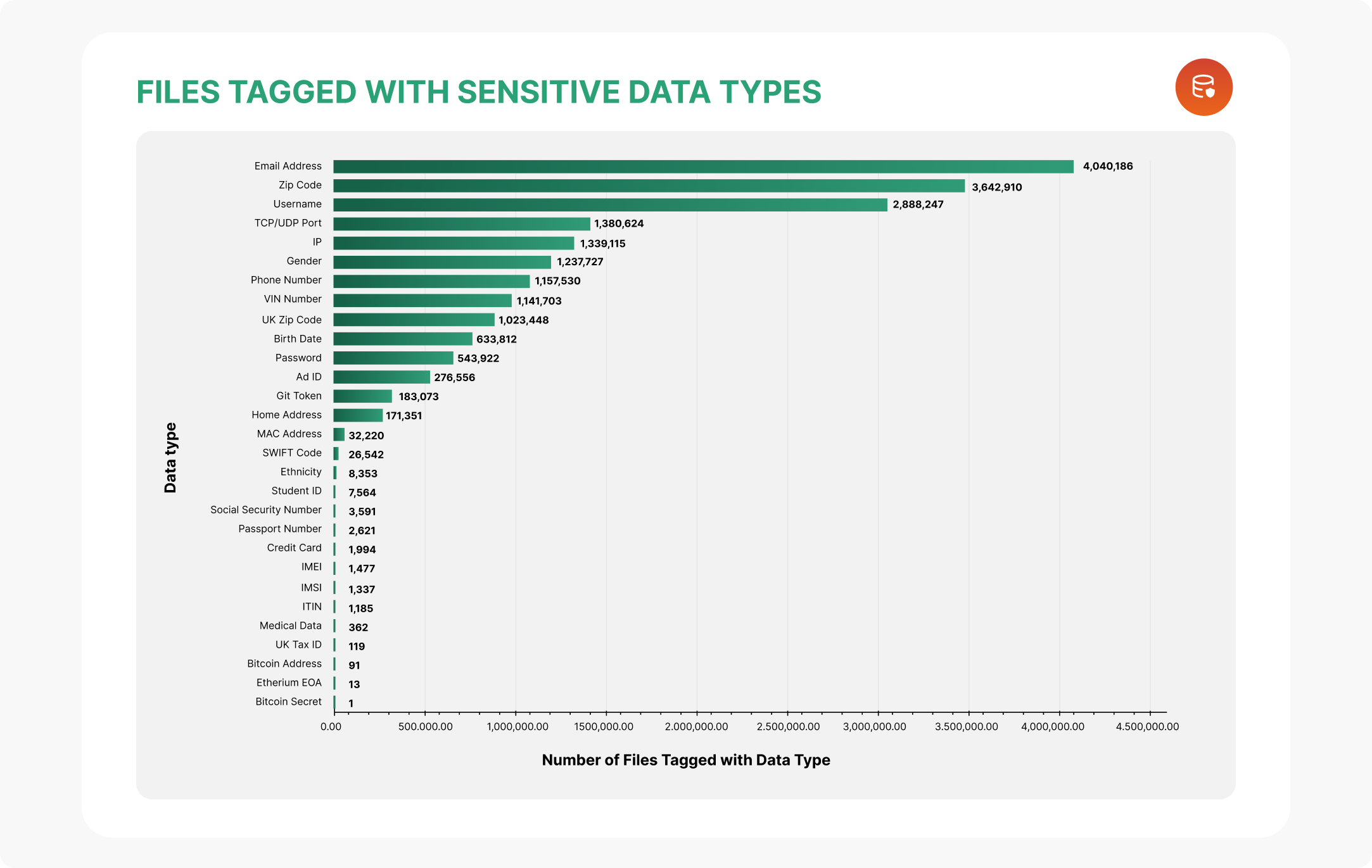
AWS S3 buckets provide a convenient and scalable solution for storing and accessing data in the cloud. However, if not properly secured, they can be susceptible to various security risks. As per the report from Laminar Research labs, 21% of all the publicly exposed S3 buckets contain sensitive data.
Image courtesy: Laminar Research Labs
In this post, I wanted to dive into the most common misconfigurations and risks involved in using S3 buckets and practical mitigation strategies.
1. Exposed or Misconfigured Buckets
a. Publicly accessible buckets: To identify publicly accessible buckets, you can use the AWS Command Line Interface (CLI) with the following command:
aws s3api list-buckets --query "Buckets[?((PublicAccessBlockConfiguration.RestrictPublicBuckets==null) || (PublicAccessBlockConfiguration.RestrictPublicBuckets==true))].Name"
To mitigate this risk, enable the public access block setting on your buckets using the following command:
aws s3api put-public-access-block --bucket YOUR_BUCKET_NAME --public-access-block-configuration "BlockPublicAcls=true,IgnorePublicAcls=true,BlockPublicPolicy=true,RestrictPublicBuckets=true"
b. Inadequate access controls: To identify buckets with inadequate access controls, you can use the AWS CLI and check the bucket policies and Access Control Lists (ACLs) for each bucket. For example:
aws s3api get-bucket-policy --bucket YOUR_BUCKET_NAME
aws s3api get-bucket-acl --bucket YOUR_BUCKET_NAME
To mitigate this risk, review and update the bucket policies and ACLs to follow the principle of least privilege. Ensure that only authorized users or roles have appropriate permissions to access the buckets.
2. Data Breaches and Unauthorized Access
a. Account compromise: To detect potential account compromises, enable AWS CloudTrail to log and monitor API activity. You can use the following command to create a new trail:
aws cloudtrail create-trail --name YOUR_TRAIL_NAME --s3-bucket-name YOUR_LOG_BUCKET_NAME
Regularly review the CloudTrail logs and set up notifications or alarms for any suspicious activities or unauthorized access attempts.
b. Insider threats: To mitigate insider threats, implement a strong authentication mechanism such as multifactor authentication (MFA) for AWS accounts. Enforce strong password policies and regularly educate employees on security best practices. Restrict access based on job roles and responsibilities to minimize the risk of insider attacks.
3. Data Loss and Corruption
a. Lack of versioning and backup strategies: To enable versioning for an S3 bucket using the AWS CLI, use the following command:
aws s3api put-bucket-versioning --bucket YOUR_BUCKET_NAME --versioning-configuration Status=Enabled
Ensure that versioning is enabled for critical buckets to retain previous versions of objects and facilitate easy recovery in case of accidental deletion or corruption.
b. Inadequate disaster recovery plans: To implement a disaster recovery plan, you can set up cross-region replication for your S3 buckets. This replicates data to a secondary bucket in a different AWS region. Use the following command to enable cross-region replication:
aws s3api put-bucket-replication --bucket YOUR_SOURCE_BUCKET --replication-configuration "Role=arn:aws:iam::YOUR_ACCOUNT_ID:role/YOUR_REPLICATION_ROLE,Rules=[{Destination:{Bucket=arn:aws:s3:::YOUR_DESTINATION_BUCKET},Status=Enabled}]"
Regularly test your disaster recovery plan to ensure its effectiveness and update it as needed.
Proactively addressing common security risks associated with AWS S3 buckets is crucial for maintaining data integrity and preventing unauthorized access. For the upcoming ransomware assessment, I would be evaluating the AWS S3 buckets within my company to identify any of the above security gaps.

